When working with Azure Container Registry (ACR) in Azure DevOps pipelines, you may encounter authorization errors when trying to push or pull Docker images. This tutorial provides multiple solutions to resolve these issues.
Service principal’s token expired
An issue that often arises with service principals or secrets that are automatically created is that the token expires and needs to be renewed. If you have an issue with refreshing the token, see Failed to obtain an access token or a valid refresh token wasn’t found.
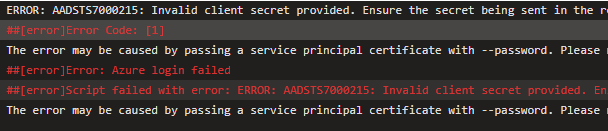
If your token expired, you could see one of the error messages:
AADSTS7000215: Invalid client secret is providedAADSTS7000222: The provided client secret keys for app '***' are expiredInvalid client id or client secret
To renew the access token for an automatically created service principal or secret:
Option 1: Edit and Re-save the Existing Service Connection
Sometimes simply re-saving the existing service connection can resolve authentication issues:
- Navigate to your Azure DevOps project
- Click on “Project settings” in the bottom left corner
- Select “Service connections” under the “Pipelines” section
- Find the existing ACR connection that you’re using in your pipeline
- Click on “Usage history” for that connection
- Click “Edit” (don’t make any changes unless necessary)
- Click “Save”
Note: Some users report that the save operation only works when following this specific path through the usage history rather than editing directly from the service connections list.
Option 2: Verify Service Principal Permissions
- In the Azure Portal, navigate to your Container Registry
- Go to “Access control (IAM)”
- Check that your service principal has at least “AcrPush” role assigned
- If not, click “Add role assignment” and assign the appropriate role
Option 3: Regenerate Service Connection Credentials
- In Azure DevOps, go to Project Settings > Service Connections
- Select your ACR service connection
- Click “Edit”
- Click “Verify connection” to test if it’s working
- If verification fails, consider regenerating the credentials:
- In Azure Portal, go to Azure Active Directory
- Find the service principal used by your connection
- Under “Certificates & secrets”, create a new client secret
- Update the service connection with the new secret
Option 4: Use Azure CLI Authentication in Pipeline
As an alternative to service connections, you can authenticate directly in your pipeline:
steps:
- task: AzureCLI@2
inputs:
azureSubscription: 'Your-Azure-Subscription'
scriptType: 'bash'
scriptLocation: 'inlineScript'
inlineScript: |
az acr login --name yourregistry.azurecr.io
docker pull yourregistry.azurecr.io/yourimage:tagOption 5: Check Pipeline Permissions
- In Azure DevOps, go to your pipeline definition
- Click on the three dots menu and select “Security”
- Verify that the build service has permission to access the service connection
- If not, grant permission to use the connection
Best Practices
- Always use managed identities when possible rather than secrets
- Regularly rotate credentials and update service connections
- Consider using task-based authentication for better security
- For production scenarios, implement credential scanning in your pipelines
By following one of these options, you should be able to resolve the unauthorized access issues when pushing or pulling Docker images from ACR in your Azure DevOps pipelines.
No responses yet